The Red Team is assigned the task of achieving a certain result agreed on with the client company. For example, the team might do everything it can to acquire management or developers’ emails.
It doesn’t matter how vulnerable the target is, or which device is targeted, all that matters is that the team explores every possibility to try and obtain the target data.
When providing this service our team of Ethical Hackers studies the target and acts just like a malicious hacker would, using all available procedures and techniques to evaluate the company’s capacity to defend itself against an attempted attack in a comprehensive and concrete way.
We provide our clients with support for all the technological components required to implement the TIBER-EU/TIBER-IT frameworks required by European DORA legislation (Threat-Led Penetration Testing, and more…).
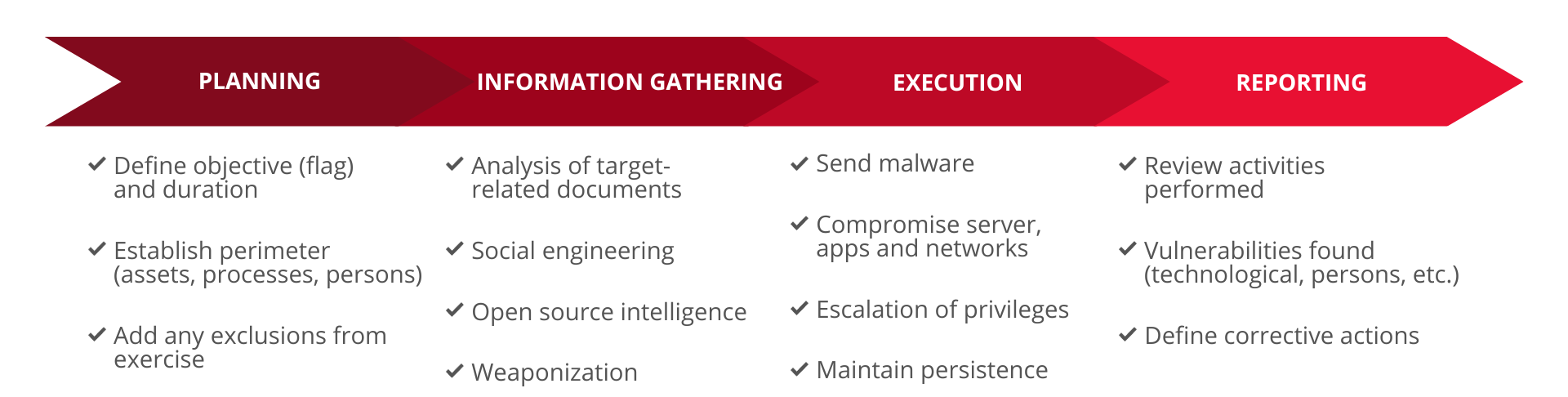

We provide a Purple Team Assessment service for all companies that have an in-house or external SOC, to evaluate the client security team’s ability to detect, respond to, and prevent cyber attacks.
We provide assistance throughout the test cycle to help our clients improve their tactics, techniques and procedures.

We review all the activities performed, the objectives achieved, any technological, procedural or human vulnerabilities found, and the necessary corrective actions our client should implement.
After our tests the company will have raised its level of defence and increased its ability to effectively respond to attacks.
Protect your company with SKIT.
Find out how our services can help you make your IT structure stronger and your company’s data and confidentiality secure.



