We design, install and configure monitoring and logging systems for services and infrastructures, to guarantee immediate results for our SOC provider clients.
We give priority to client company method learning, which makes the IT systems implemented more effective in the long term, optimizing the company’s investment.

We configure and set up the monitoring and logging systems the company needs to anticipate any harmful activities by malicious hackers.
We provide the client’s SOC with all the assistance needed to autonomously and effectively manage the system, exponentially increasing the security of the company’s IT infrastructure.
Over 90% of data breaches are caused by human error; that’s why we put people first.
When you put your trust in us you won’t be purchasing a ready-made package, it will be one tailor-made to meet your needs.
We give priority to client company method learning, which makes the IT systems implemented more effective in the long term, optimizing the company’s investment.
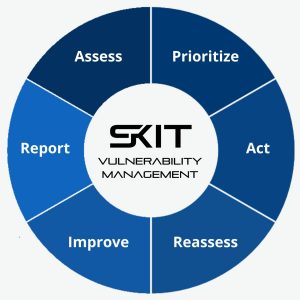
Protect your company with SKIT.
Find out how our services can help you make your IT structure stronger and your company’s data and confidentiality secure.




