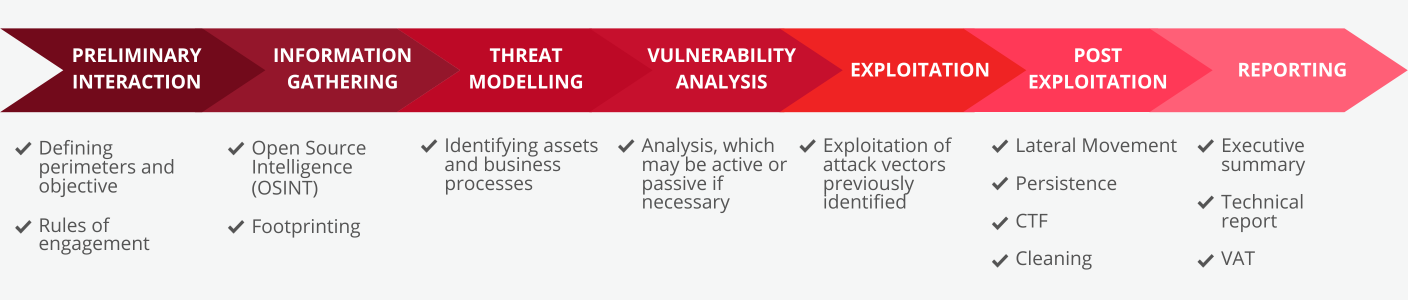
Over the years we’ve adopted a hybrid approach, combining the latest, most advanced methods developed by the scientific community with the internal skill-set of our Ethical Hacker and R&D team.
This makes the service we provide highly effective, minimizing the risk of “false positives”. Our Security Assessments have the following goals:
- reveal any defects and flaws in target systems
- quantify the real impact and damage for the company
- define effective countermeasures

We find and classify security flaws in a system or network which, if exploited, could be used to gain access to sensitive company data or even take control of systems.
The network penetration test simulates a real attack on the company and provides critical information on potential weak points hackers could potentially use to gain access.
We evaluate the security of commercially available or in-house developed web-based applications to find out whether they’re vulnerable to internal or external attacks (such as malicious users or anonymous attackers).
Vulnerability identification, validation of existing security policies, internet-facing resource and system integrity testing, observance of compliance requirements.
Companies face a considerable number of obstacles when protecting sensitive data in the cloud.
We have years of experience in security analysis with a variety of cloud services, in particular Amazon AWS, and complex container infrastructures, including: cloud console configurations, Identity Access Management (IAM), strong authentication and login credentials, bucket visibility, etc.
Nello svolgimento dell’attività, adottiamo linee guida e standard riconosciuti a livello internazionale, così come metodologie proprietarie. Questi i 4 principali:
– PTES (Penetration Testing Execution Standard)
– OSTTMM (Open Source Security Tester Methodology Manual)
– OWASP (Open Web Application Security Project)
– SKIT HybridST (SKIT Hybrid Security Testing)













We check for vulnerabilities in common authentication and encryption protocols like WEP, WPA and 802.1x that can be exploited to gain unauthorized wireless access, and for any Rogue Access Points.
These tests are performed on site, as the pentester must be within range of the Wi-Fi signal to run the test.
For SKIT the human factor is a fundamental component, both in our relationship with clients and when performing Penetration Tests!
Protect your company with SKIT.
Find out how our services can help you make your IT structure stronger and your company’s data and confidentiality secure.